Blockchain
Top 5 Blockchain Protocols For End-to-End Transaction Security
Credit : cryptonews.net
As blockchain adoption grows, so do dangers corresponding to front-running assaults, token scams, and cross-chain vulnerabilities. Blockchain safety protocols are vital on this regard, guaranteeing that each step of a transaction – from initiation to affirmation – is protected. Understanding end-to-end transaction safety is vital for customers and builders to forestall losses and guarantee safe, uninterrupted community interactions. This text examines the important thing protocols that may guarantee safe blockchain transactions in 2024.
On this information:
- High 5 Blockchain Protocols
- What’s end-to-end transaction safety?
- Is it sufficient to safe transactions with blockchain safety protocols?
- Often requested questions
High 5 Blockchain Protocols
Briefly, among the finest blockchain safety protocols in 2024 embody:
- Omnia Protocol – Frontrunning safety with personal mempools
- LayerZero – Personal relays for safe inter-chain communications
- Chainlink CCIP – Multi-layer validation for token transfers
- Wormhole – Guardian nodes for cross-chain transaction safety
- Cosmos Hub (IBC Protocol) – Safe asset transfers with Tendermint consensus
Let’s discover every blockchain safety protocol intimately.
1. Omnia Protocol: Greatest for stopping exploits
Omnia Protocol ensures blockchain customers and builders get pleasure from safe and personal entry to networks with out concern of frontrunning, token scams, or malicious interactions.
By defending transaction knowledge from initiation to completion, Omnia delivers end-to-end safety and retains each blockchain operation confidential.
Customers: Omnia Protocol
The way it works?
Omnia acts as a monitored tunnel for blockchain transactions. When a person interacts with a blockchain via Omnia’s personal RPC endpoints, the info is hidden from the general public, defending it from attackers. These personal mempools forestall bots from conducting transactions or intercepting delicate data.
Moreover, Omnia detects honeypots – rip-off tokens designed to trick customers – by analyzing sensible contracts and transaction knowledge in actual time.
Omnia can be blockchain agnostic and helps steady transaction monitoring and a number of networks, guaranteeing the broadest potential safety protection.
Plus factors
- Prevents entrance working assaults: Personal RPCs preserve transactions hidden from bots.
- Blocks rip-off tokens: Honeypot detection prevents customers from interacting with fraudulent tokens.
- Multi-chain help: Works on totally different blockchains and supplies flexibility.
Disadvantages
- Technical setup: Customers might have time to know personal RPCs and honeypot protections.
- Node Dependency: Requires constant participation of nodes for uninterrupted entry
2. LayerZero: Greatest for safe cross-chain transactions
LayerZero ensures that transactions between totally different blockchains happen securely and with out interruptions. Cross-chain transactions typically introduce new dangers, corresponding to frontrunning and incomplete transfers, however LayerZero eliminates these vulnerabilities by securing each a part of the transaction – from initiation on one blockchain to affirmation on one other.
The way it works?
LayerZero maintains pace and safety through the use of a mix of ultra-light nodes (ULNs), oracles, and relayers. Consider it like sending a bundle via a trusted courier community, the place the couriers (relayers) and validators (oracles) affirm that the bundle reaches its vacation spot intact, with out the intervention of outsiders.
Extremely-light nodes (ULNs) validate transactions with out requiring the info from all the blockchain, maintaining the community versatile and sustaining safety.
Relayers transmit the transaction knowledge between blockchains and preserve it hidden from public data in order that nobody can intercept the info or manipulate the transaction.
Oracles independently confirm transactions on each the supply and vacation spot chains, sustaining knowledge integrity even throughout cross-chain swaps.
By way of end-to-end upkeep of transaction safety, the personal relayers shield transaction knowledge from tampering or interception, whereas the ULNs guarantee safe validation.
Moreover, every community element capabilities independently, decreasing the chance of system-wide vulnerabilities. That is all due to the resilient modular design.
Plus factors
- Progressive mitigation: Personal relayers preserve transactions out of public mempools.
- Quick cross-chain execution: Extremely-lightweight nodes pace up transactions with out compromising safety.
- Dependable verification: Oracles ensures that each transaction is correctly validated, defending person property.
Disadvantages
- Complicated setup: Customers might initially discover the structure with relays and oracles obscure.
- Dependency on validators: Though decentralized, the operation of LayerZero depends on validators functioning correctly.
3. Chainlink CCIP: Greatest for securing token transfers
Chainlink’s Cross-Chain Interoperability Protocol (CCIP) supplies a dependable method to switch tokens between blockchains whereas stopping switch errors or tampering. By verifying transactions at varied factors, CCIP ensures that each switch is safe from begin to end, making it a vital instrument for safe cross-chain operations.
Chainlink Protocol: Chainlink
The way it works?
CCIP acts as a checkpoint system for blockchain transactions. When sending tokens between networks, oracles and validators work collectively to substantiate every step of the method.
Think about sending a bundle the place each publish workplace stamps it alongside the route. This manner you possibly can make sure that the bundle has not been tampered with earlier than it reaches its vacation spot.
Chainlink CCIP makes use of multi-point validation, personal communication channels, and versatile token processing for safer transfers and error prevention.
Plus factors
- Entrance run safety: Retains transactions out of public view to keep away from interference.
- Safe token transfers: Validates transactions at a number of factors to forestall errors or losses.
- Flexibility throughout the chain: Helps many networks for seamless asset motion.
Disadvantages
- Studying curve: Customers might have time to know programmable transfers.
- Trusting oracles: The method is determined by the right functioning of validators and oracles.
4. Wormhole: Greatest with guardian verification
Wormhole permits property and knowledge to be moved securely between a number of blockchains, decreasing the dangers related to cross-chain transactions.
With its Guardian Node system, Wormhole ensures that each transaction is independently verified, blocking unauthorized or tampered transfers and guaranteeing the transaction stays safe from begin to end.
Wormhole interface: Wormhole
The way it works?
Wormhole capabilities as a bridge between blockchains and facilitates the switch of property utilizing surveillance nodes. Consider the surveillance junctions as checkpoints on a freeway: each time a automobile (transaction) passes, it’s inspected to make sure it meets all security requirements.
When a transaction is initiated on one blockchain, the Guardian nodes validate it earlier than it reaches the vacation spot blockchain. In the event that they uncover discrepancies, the transaction is rejected in order that solely reliable transfers are processed. This ensures that end-to-end transaction safety is maintained even when property or knowledge are transferred throughout totally different networks.
Wormhole is likely one of the few blockchain safety protocols that depend on a decentralized bridge design. Moreover, there may be entry to asset restoration instruments.
Plus factors
- Guardian verification: Protects transfers by controlling every step individually.
- Decentralized safety: Reduces dependency on a single validator, stopping system-wide vulnerabilities.
- Restoration mechanisms: Supplies instruments for dealing with failed or caught transactions.
Disadvantages
- Bridging vulnerability dangers: Like different chain bridges, Wormhole is uncovered to evolving assault strategies.
- Complicated setup: Customers might have time to know the Guardian Node system.
Cosmos Hub: Greatest for safe asset transfers utilizing the IBC protocol
The Cosmos Hub allows safe cross-chain transactions utilizing the Inter-Blockchain Communication (IBC) Protocol. It permits property and knowledge to maneuver securely between related networks, sustaining integrity all through the transaction. Cosmos reduces the chance of incomplete or tampered transmissions and ensures that each step – from sending to receiving – is dealt with securely.
The way it works?
The IBC protocol capabilities as a safe supply community. When a person sends tokens from one blockchain to a different, IBC ensures that each chains validate the switch earlier than it’s accomplished. Consider it as a two-way handshake: the sending chain locks the tokens, and the receiving chain solely points an equal quantity as soon as step one is confirmed. If an issue arises throughout the course of, the transaction is halted, defending the property from loss.
IBC additionally makes use of Tendermint consensus to take care of belief and consistency between blockchains, guaranteeing transactions are correctly validated with out delays or manipulation.
Plus factors
- Prevents asset loss: Two-way validation ensures property are by no means misplaced in transit.
- Quick and constant: Tendermint consensus supplies quick validation with out compromising safety.
- Proof against downtime: IBC can deal with community outages and shield property till restoration.
Disadvantages
- Community coordination: Requires coordination between a number of blockchains, which might introduce complexity.
- Restricted adoption: Some networks nonetheless combine IBC, limiting present use instances.
What’s end-to-end transaction safety?
Finish-to-end transaction safety ensures that each transaction, from initiation to completion, is protected towards dangers corresponding to manipulation, entrance working or incomplete execution.
This idea ensures that no unauthorized entity can disrupt or alter a transaction, giving customers full confidence of their blockchain actions.
With out correct end-to-end safety, blockchain transactions run the chance of being uncovered to entrance working, phishing or incomplete transfers.
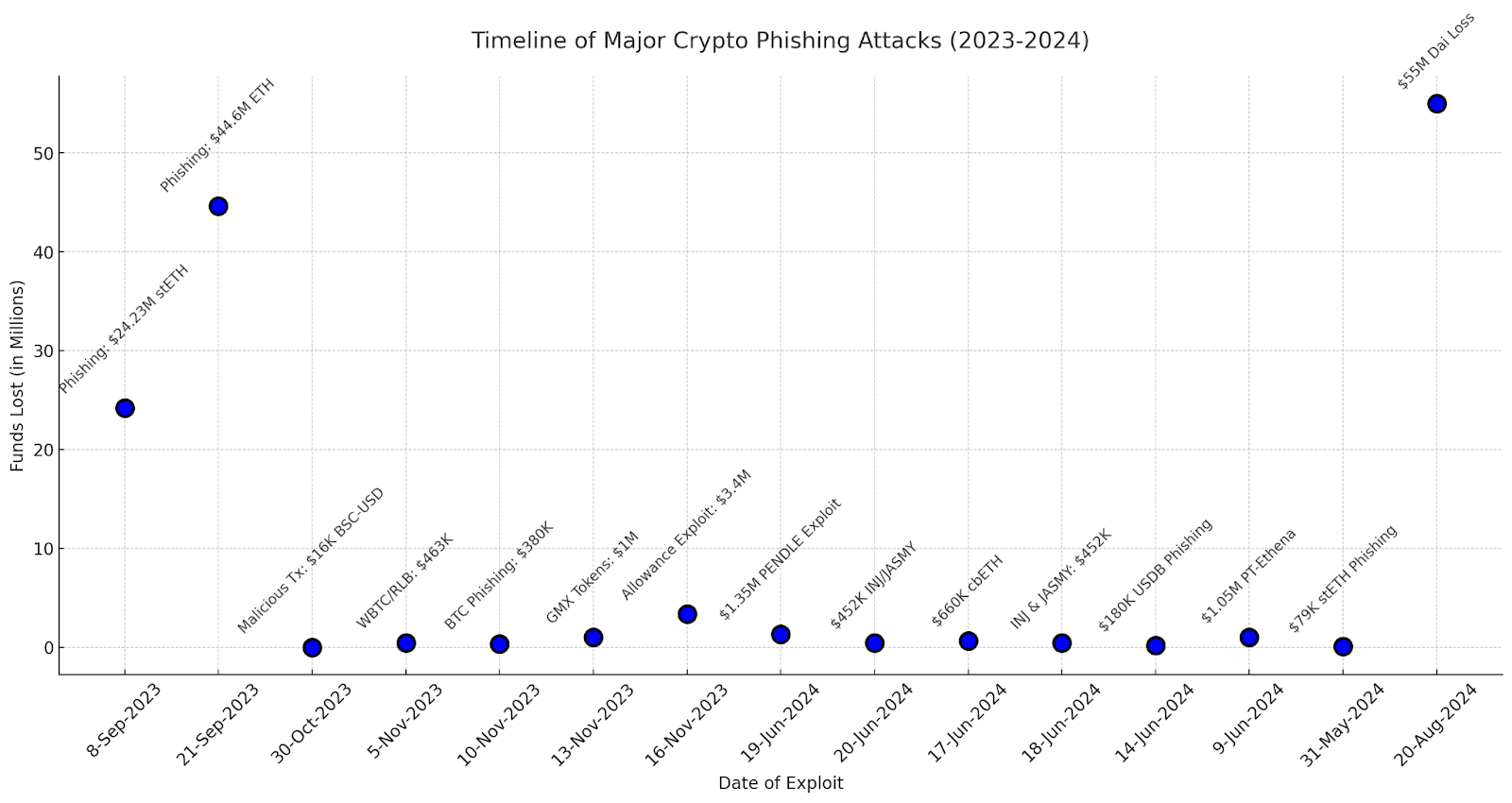
Timeline of main phishing occasions: BIC
Blockchain safety protocols be sure that customers’ funds stay protected, that interactions with sensible contracts are dependable, and that no knowledge is leaked or manipulated alongside the way in which.
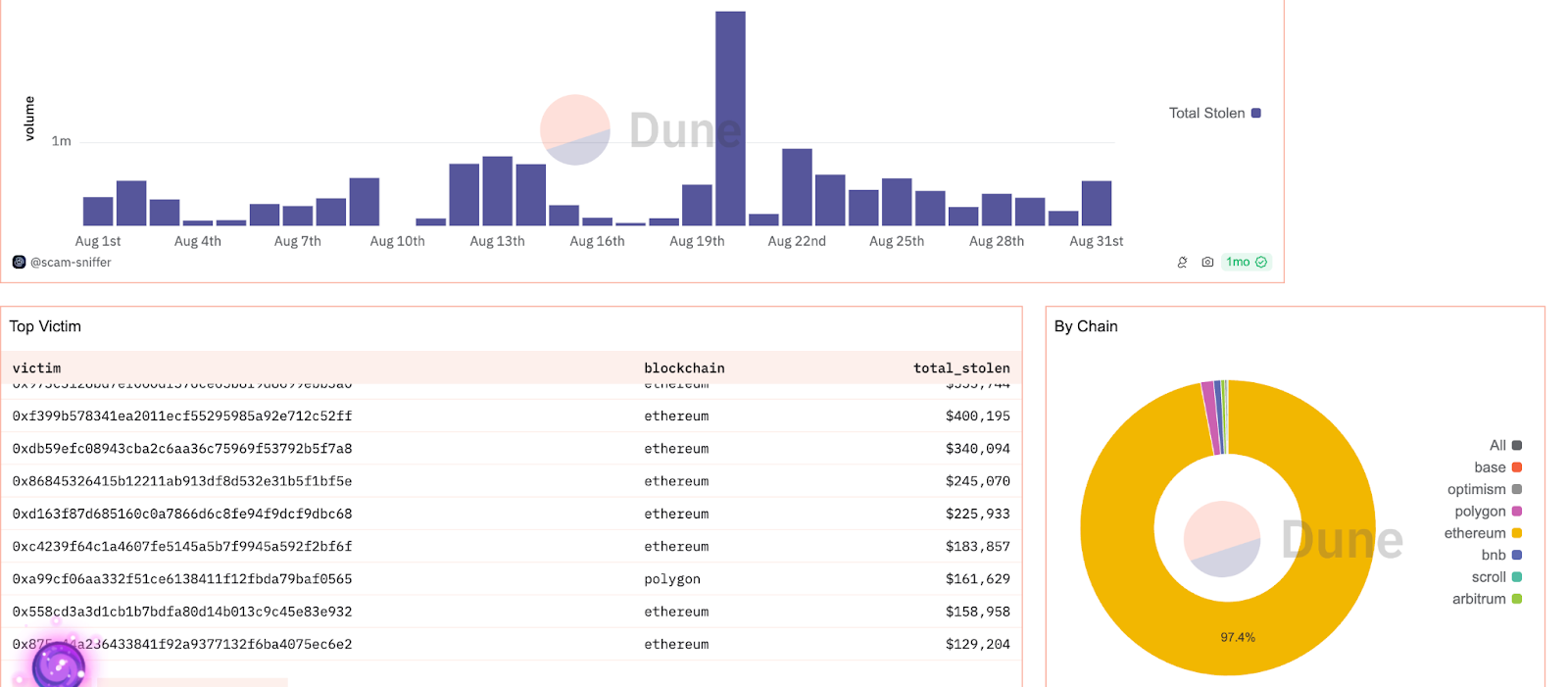
Latest phishing developments: Dune
Is it sufficient to safe transactions with blockchain safety protocols?
Blockchain safety protocols are an important step in direction of safe transactions. Nonetheless, they might not be enough on their very own. Whereas these protocols present end-to-end safety by stopping tampering and authenticating knowledge, evolving threats require fixed upgrades.
A multi-layered strategy – together with person consciousness, audits and extra safeguards – ensures stronger safety and belief inside decentralized networks.
-

 Meme Coin8 months ago
Meme Coin8 months agoDOGE Sees Massive User Growth: Active Addresses Up 400%
-

 Blockchain1 year ago
Blockchain1 year agoOrbler Partners with Meta Lion to Accelerate Web3 Growth
-

 Videos1 year ago
Videos1 year agoShocking Truth About TRON! TRX Crypto Review & Price Predictions!
-

 NFT11 months ago
NFT11 months agoSEND Arcade launches NFT entry pass for Squad Game Season 2, inspired by Squid Game
-

 Meme Coin1 year ago
Meme Coin1 year agoCrypto Whale Buys the Dip: Accumulates PEPE and ETH
-

 Solana5 months ago
Solana5 months agoSolana Price to Target $200 Amid Bullish Momentum and Staking ETF News?
-

 Ethereum1 year ago
Ethereum1 year ago5 signs that the crypto bull run is coming this September
-

 Videos4 months ago
Videos4 months agoStack Sats by Gaming: 7 Free Bitcoin Apps You Can Download Now