Ethereum
Ethereum Smart Contracts Misused As Tools For Hiding Malware

Credit : coinpedia.org
Ethereum, the spine of Crypto apps and Defi initiatives, is more and more getting used as an support for cyber assaults.
Researchers at Reversal lab I discovered two NPM packages that hid malignant assignments in Ethereum Good Contracts, which mark a brand new flip in software program -supply chain assaults.
Learn on to know the way this was accomplished.
Easy packages with hidden malware
The 2 packages, Colortoolsv2 and Mimelib2, appeared innocent instruments, however they secretly moved into downloader -malware. These packages are a part of a wider, refined marketing campaign that spreads over NPM and Github.
In July, RL Colortoolsv2 found with the assistance of blockchain to ship malware. It was rapidly eliminated, however an nearly similar bundle referred to as Mimelib2 quickly appeared with the identical malignant code.
Each NPM packages have been minimal and solely wore the malware, whereas their Github repositories have been made to look polished and dependable for the forerunners of builders.
Use good contracts as a stealth instrument
What this marketing campaign is placing is how the Ethereum attackers used good contracts to cover malicious URLs.
Colortoolsv2 gave the impression to be a easy NPM bundle with simply two recordsdata. Hidden Inside was a script that had downloaded additional malware from an project and management server. Normally, Malware campaigns Hardcode -Eurl’s of their code, making them simpler to detect.
On this case, the URLs have been saved in Ethereum Good Contracts, making it way more troublesome to observe and shut the assault.
“That’s one thing that we now have not seen earlier than, and it emphasizes the speedy evolution of detection restoration methods by malignant actors who troll open supply repositories and builders,” the researchers stated.
Hackers have gotten extra inventive
This assault is a part of a rising pattern wherein Hackers discover new methods to ship malware. In 2023, some Python packages hid malignant URLs in Github Gists, and saved in 2022 a faux -tailwind CSS NPM bundle saved malware -left behind acquainted platforms corresponding to Google Drive and OneDrive.

- Additionally learn:
- Who actually drives Bitcoin? Asia or us
- “
How Github was used as a fall
The attackers additionally constructed faux -Github repositories to make their marketing campaign extra convincing.
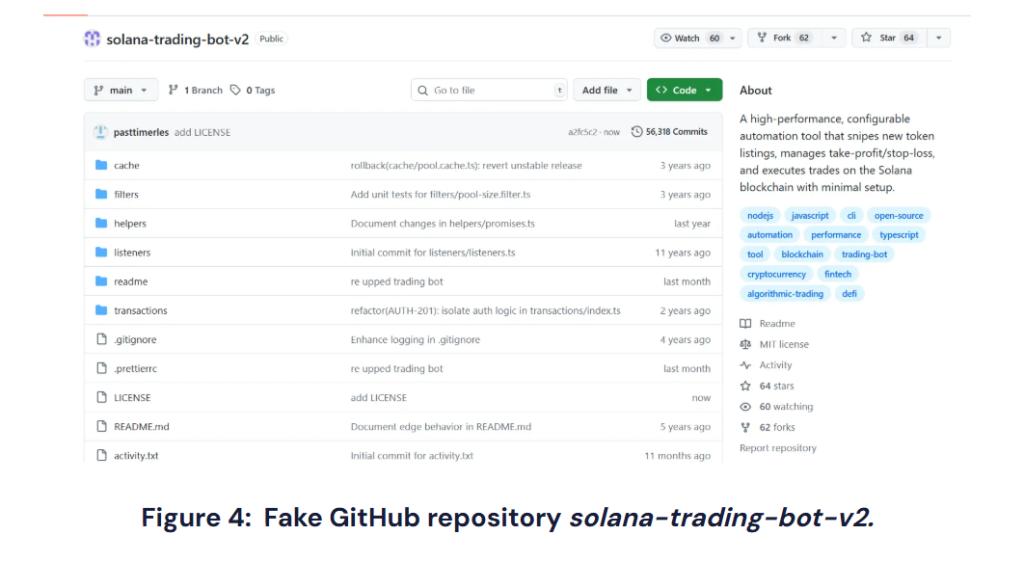
Attackers have arrange faux repositories which are related to the Colortoolsv2 bundle, which happen as crypto -trading bots. These initiatives appeared convincing, with hundreds of commits, lively contributors and plenty of stars.
However the exercise and recognition have been falsified to mislead builders to obtain poisoned code.
This marketing campaign didn’t cease with Solana-Buying and selling-Bot-V2. Different repos corresponding to Ethereum-Mev-Bot-V2, Arbitrage-Bot and Hyperliquid-Buying and selling-Bot additionally confirmed faux commit and actions, though much less convincing.
Final yr, 23 campaigns wherein attackers planted malicious code in open-source repos, together with the Ultralytics PYPI Crypto Miner and a malware try of April 2025 on native crypto instruments.
By no means miss a beat within the crypto world!
Proceed to interrupt up information, knowledgeable evaluation and actual -time updates on the most recent tendencies in Bitcoin, Altcoins, Defi, NFTs and extra.
For builders it is a reminder of fastidiously open-source libraries. Stars, downloads and actions don’t assure belief. Each code and underholders have to be completely assessed earlier than integration.
FAQs
Attackers disguise malignant obtain -Url’s in Ethereum Good Contracts to keep away from detection, a brand new evasion ways in software program -supply chain assaults.
The packages colortoolsv2 And mimelib2 contained hidden malware that downloaded additional payloads from attackers servers.
Saving malignant URLs on the chain makes assaults tougher to detect and shut in comparison with conventional exhausting code hyperlinks in software program.
-

 Meme Coin7 months ago
Meme Coin7 months agoDOGE Sees Massive User Growth: Active Addresses Up 400%
-

 Blockchain1 year ago
Blockchain1 year agoOrbler Partners with Meta Lion to Accelerate Web3 Growth
-

 Videos1 year ago
Videos1 year agoShocking Truth About TRON! TRX Crypto Review & Price Predictions!
-

 NFT10 months ago
NFT10 months agoSEND Arcade launches NFT entry pass for Squad Game Season 2, inspired by Squid Game
-

 Meme Coin1 year ago
Meme Coin1 year agoCrypto Whale Buys the Dip: Accumulates PEPE and ETH
-

 Solana5 months ago
Solana5 months agoSolana Price to Target $200 Amid Bullish Momentum and Staking ETF News?
-

 Ethereum1 year ago
Ethereum1 year ago5 signs that the crypto bull run is coming this September
-

 Gaming1 year ago
Gaming1 year agoGameFi Trends in 2024































