NFT
Nearly half of stolen crypto remains unspent, data shows

Credit : crypto.news
About 46% of the hacked funds are inactive on the chain, which recommend alternatives for restoration after incident, analysts say at World Ledger.
Hackers are quick, however the methods they’re chasing are nonetheless catching up. A brand new report By blockchain inflooring firm World Ledger, primarily based on tons of of incidents on chains, exhibits that stolen funds in lots of instances on cash laundering earlier than the hack is even introduced.
On common, it takes 43.83 hours of the preliminary infringement on the chain till the incident has been reported by the sufferer undertaking or an exterior researcher, in keeping with the report shared with crypto.information. Within the meantime, Hackers have a tendency to maneuver stolen funds to the primary recognized entity, comparable to an alternate, a cryptomixer or a decentralized monetary protocol, inside 46.74 hours.
The longest delay, nonetheless, is the window between public disclosure and the interplay of the attacker with a white operation service, which is on common 78.55 hours, which means that funds are sometimes already shifting nicely earlier than a hack turns into typically recognized.
‘Not a transparent playbook right here’
In complete, the World Ledger researchers measured 4 vital timelines for tons of of incidents. The time of infringement on the financing of motion, from infringement on reporting, from infringement to interplay of the primary entity and of public disclosure of cash laundering actions. Each delay additionally tells its personal story.
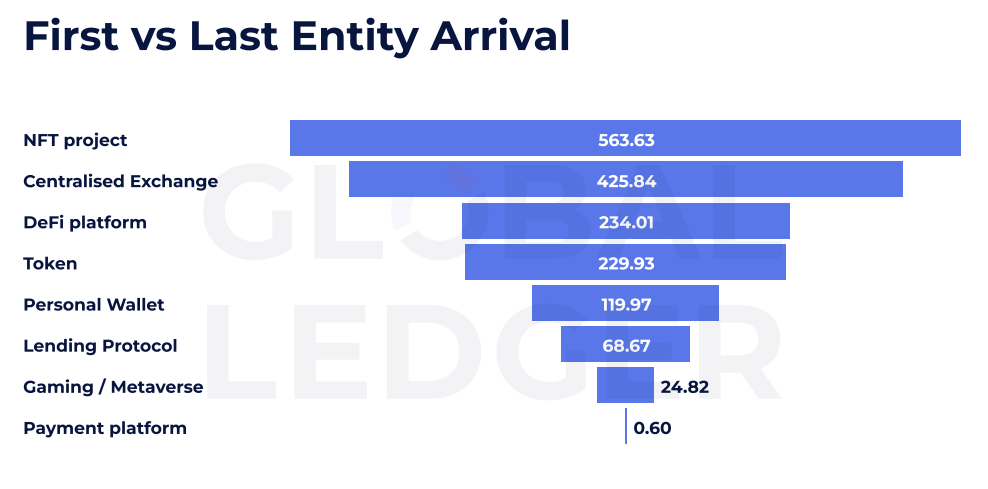
Assaults geared toward NFT initiatives, for instance, present the slowest fund actions. On common it takes 563.63 hours – or nearly 24 days – for funds from these exploits from the primary to the final recognized entity within the cash laundering chain. That’s greater than double the common delay that’s seen in centralized alternate -related hacks, which clock round 425 hours.
Co-founder and CEO of World Ledger instructed Lex Fisun to crypto.information in an unique remark that the lengthy delay-in the case of NFTs-not is barely about low liquidity, as a result of these tokens are “distinctive and harder to load.”
“There isn’t a clear playbook right here, washing normally consists of washing or social engineering. Consider the exploitation of the idols, the place the attacker has emptied $ 340,000 in Steth however bought caught to the corresponding NFTs.”
Lex Fisun
The report emphasizes how cash laundering differ, relying on the operated undertaking. Defi platforms and tokens normally see funds shifting by the cash laundering of channels inside 230 hours, whereas cost platforms present the quickest lead time: on common solely 0.6 hours. Gaming and Metaverse exploits are additionally among the many sooner streams, which transfer for lower than 25 hours.
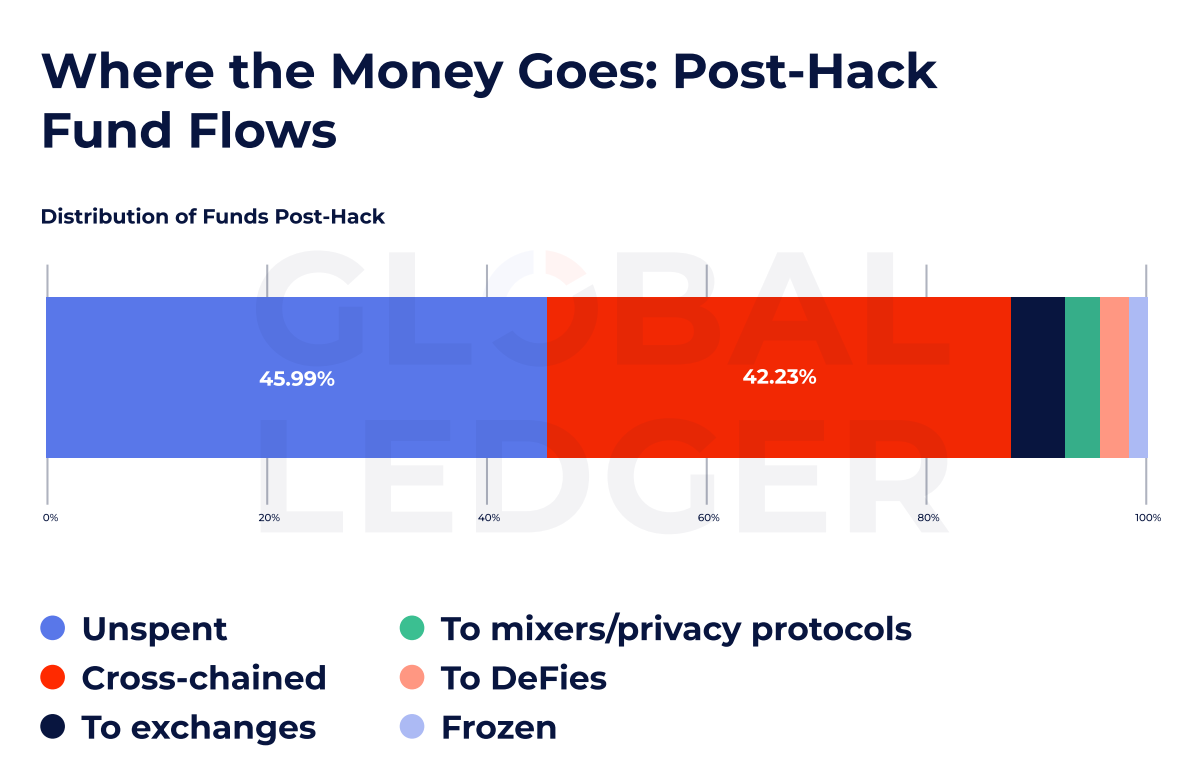
Regardless of the velocity and fragmentation of fund flows, a shocking quantity of hacked property stays untouched. In accordance with the info, nearly 46% of the stolen funds are nonetheless not stimulated, which means that vital prospects for fixed monitoring and potential restoration, lengthy after an incident takes place.
Traces
Though many funds are inactive, a rising share slides by harder cross -chain routes. The report exhibits that 42.23% of the stolen funds had been moved over chains and bypassed chain -specific safety methods.
Fisun defined that cross-chain bridges “have already turn into the most effective cash laundering” for the expiry of chain-specific monitoring. And though repeated abuse AML can take management, the Twister -Money Case proves one factor: “Sanctions shift techniques, not the query,” Fisun added.
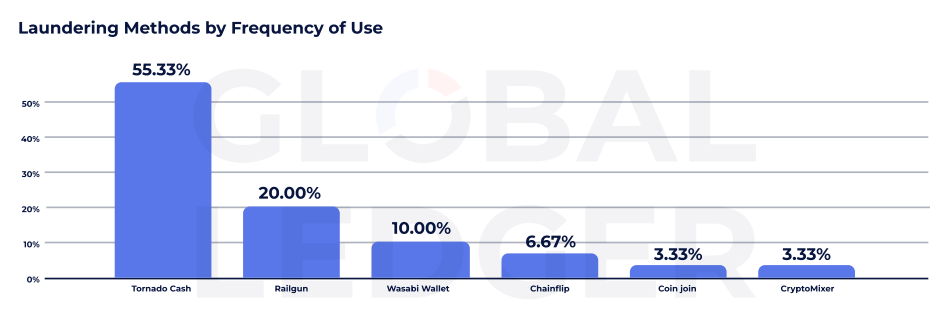
The info from World Ledger additionally present that Twister -Contant Cash stays the dominant cash laundering protocol, which is utilized in greater than 50% of the instances adopted by the corporate. Regardless of the American treasury sanctions In 2022, and the growing strain of regulators worldwide, the service continues to play a central position in cash laundering.
Its use once more after a call by the American court docket had annulled the sanctions on constitutional grounds in 2024.
Different privateness instruments additionally acquire energy. Railgun, for instance, was utilized in 20% of the instances, whereas Wasabi pockets appeared in 10%. Chainflip, Coinjoin and Cryptomixer had been every concerned in lower than 7% of cash laundering, the info exhibits.
Attackers are getting smarter
Fisun famous that slower flows on account of centralized exchanges – now on common greater than 425 hours – not essentially solely replicate higher compliance.
It’s each, mentioned the World Ledger CEO, including {that a} slower timeline “isn’t a malfunction, it’s due to design” as a result of attackers use property, cut up hop chains and privateness protocols to maneuver stolen funds by CEX’s who attempt to postpone streams which might be shadow. “
Solely a small a part of the funds are frozen by enforcement or compliance groups. The report means that actual -time reactions stay uncommon, even when evaluation and monitoring instruments make progress.
Though the figures point out steady challenges, in addition they underline the place defenders can get a lead. The instances – typically measured in days – present that there’s nonetheless room to behave earlier than stolen funds disappear utterly.
-

 Analysis4 months ago
Analysis4 months ago‘The Biggest AltSeason Will Start Next Week’ -Will Altcoins Outperform Bitcoin?
-

 Blockchain1 year ago
Blockchain1 year agoOrbler Partners with Meta Lion to Accelerate Web3 Growth
-

 Meme Coin10 months ago
Meme Coin10 months agoDOGE Sees Massive User Growth: Active Addresses Up 400%
-

 Videos1 year ago
Videos1 year agoShocking Truth About TRON! TRX Crypto Review & Price Predictions!
-

 NFT1 year ago
NFT1 year agoSEND Arcade launches NFT entry pass for Squad Game Season 2, inspired by Squid Game
-

 Web 34 months ago
Web 34 months agoHGX H200 Inference Server: Maximum power for your AI & LLM applications with MM International
-

 Meme Coin1 year ago
Meme Coin1 year agoCrypto Whale Buys the Dip: Accumulates PEPE and ETH
-

 Videos6 months ago
Videos6 months agoStack Sats by Gaming: 7 Free Bitcoin Apps You Can Download Now























